Prepare for Quantum computing effects on information security
Digipoolin ja VTT:n yhteisprojektissa koostettiin tietoa elinkeinoelämän varautumisen tueksi sekä annettiin suosituksia toimenpiteiksi, joita tulee nyt lähteä toteuttamaan organisaatiossa kuin organisaatiossa.
Benefits and development of quantum computing
Quantum computers have the potential to solve problems that are practically impossible or extremely difficult for traditional supercomputers. With quantum computers, we can tackle enormous challenges, which has gathered significant interest in their development, and indeed, this development is happening on a massive scale. For example, China is investing tens of billions of euros in quantum technology development.
One does not need to be a clairvoyant to see that, given the substantial investment, the realization of quantum computing is expected to occur within a relatively short timeframe. As we begin to reap the benefits, business dependencies on the applications solved by quantum computing will grow. This will likely lead to an increased need to ensure the availability of quantum computing capacity, making it critical infrastructure for national security and for any business. Quantum computing capacity can already be utilized as a cloud service, emphasizing the importance of connectivity. Consequently, we may see more entities developing their capabilities in this field.
Finland is currently a pioneer in quantum computer development, with several companies actively involved in this area. This can be seen as a result of university research activities, which is highly favorable. However, this progress is overshadowed by the fact that, as a small country, Finland produces very few experts in the field. As a result, domestic companies must rely on international labor, and as these companies grow, their ties to Finland may weaken. From this perspective, Finland must nationally invest broadly in the development of expertise to meet the needs of research and business activities, as well as in preparedness measures that need to be initiated now. With our current foundation, we have excellent opportunities to remain leaders in the field, provided that investments are made.
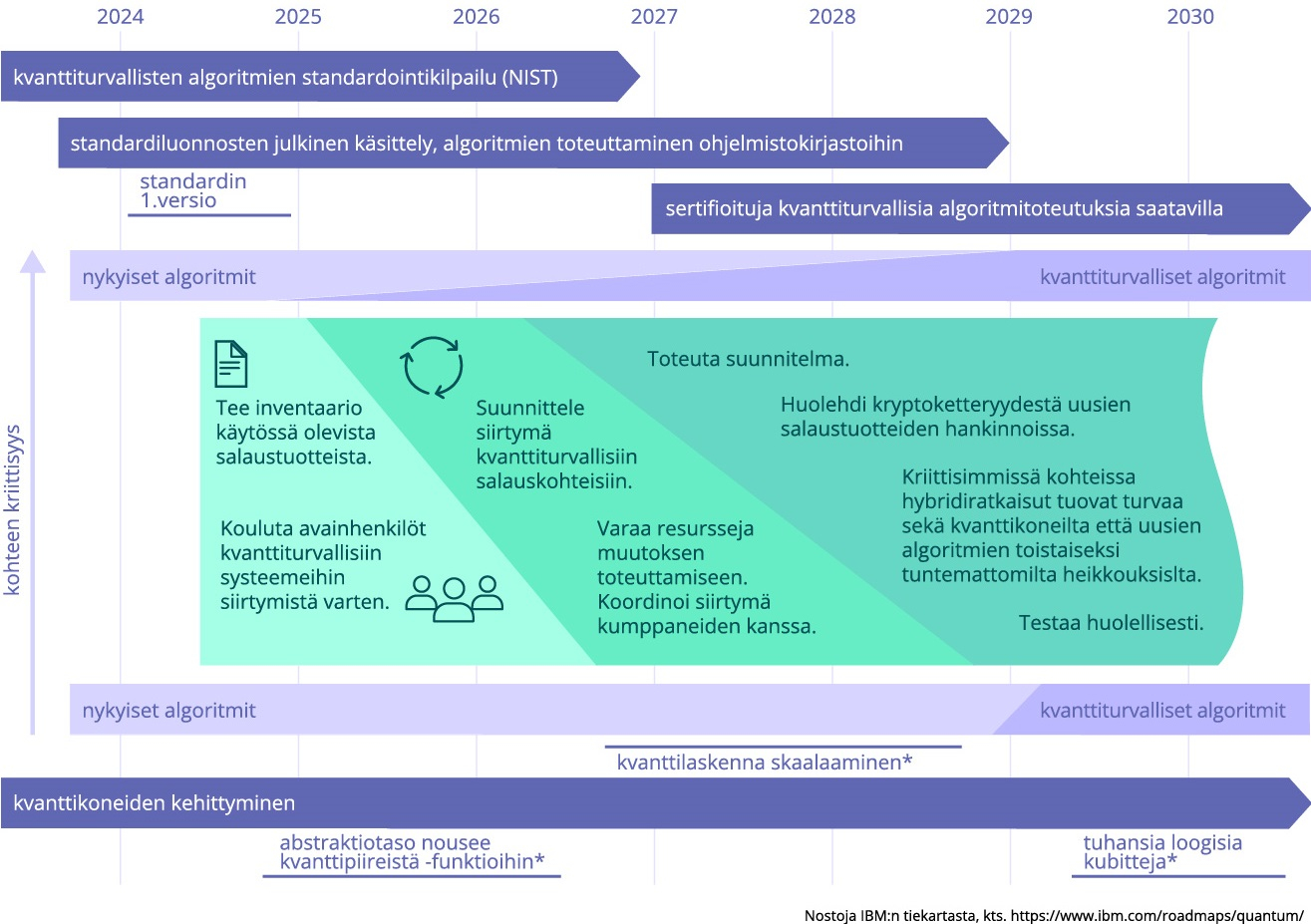
Estimates of the timeline for quantum computing development milestones vary, but the consensus seems to be that by around 2030, quantum computing capabilities will render traditional computing methods and solutions obsolete. Given that quantum computing is already available as a commercial service, it is evident that its business opportunities should be explored now, while also preparing for the cybersecurity threats that advancements in quantum computing may bring. Fortunately, quantum-resistant encryption algorithms have also progressed, and standardizations in this area are expected as early as this year.
The Impacts of quantum computing development
Today, data is encrypted using both symmetric (secret key) and public key methods. With the advancement of quantum computing, the threat arises that efficient computation could break solutions based on public key methods. The business development of criminals (or states) may already be targeting this, aiming to exploit new technology to generate value for their operations.
Public key methods are used, for instance, in electronic signatures, and many encryption methods used on the Internet, such as TLS (Transport Layer Security) and PGP (Pretty Good Privacy), are based on public key encryption. In other words, the immense computational power of quantum computers can be misused, thus posing a significant threat to current data and communication encryption solutions. There are also geopolitical threats to consider, as the economic power alone of a hostile state possessing a quantum computer could threaten the national security and supply security of other states.
The threat extends to various solutions and information that require encryption. Examining information that, according to domestic legislation, must be kept secret for years reveals threats that, by the estimated timeline of around 2030, data encrypted and stolen now could be decrypted, raising many concerning thoughts. This threat, combined with knowledge of how well (or rather, how poorly) companies have managed their encryption solutions or understand the value of the data they manage, suggests that NOW is indeed the time to start preparing and ensuring that business can continue even in this disruptive situation.
Recommendations for Preparing for the Development of Quantum Computing
How should one properly prepare? Preparatory measures can be divided into three main areas:
- Conduct an Inventory.
- Identify the encryption solutions used within the organization, covering both software and hardware.
- Identify at least the key encrypted data, classify it according to the need for confidentiality, and prioritize the need for re-encryption.
- Plan the Transition to Quantum-Safe Solutions.
- Develop a detailed plan for updating encryption systems based on the criticality of the systems and the actual risks.
- Implement the Transition According to the Plan, Starting with the Most Critical Areas Based on Risks.
Estimates for implementing this "transition project" vary, but in the worst case, it could take years and encompass a period during which both traditional and newer encryption algorithms must be used. This requires expertise in both, or at least an understanding sufficient to demand the right solutions. It is possible that the development of quantum computing will outpace the ability to complete this transition, but what is certain is that preparation must begin now! And it should start with an inventory, especially if one has not been done yet or is incomplete.
You can download the recommendation document produced in the project from the HVK website.
Download the guidelines with recommendations here!
The document provides an overview of the literature and sources underlying this writing and presents the findings of a survey on the preparedness of companies within the Security of Supply Organization. Finally, it offers recommendations for preparatory measures. Plan your own roadmap and start implementing it!